Food Fraud
Food fraud: Possibilities and opportunities for risk minimisation in complex networked value-added chains
DLG Expert report 11/2018
Author:
Dr.-Ing. Andreas Müller,
graduate physicist,
Andreas.Mueller@worxplus.de
Contact:
Bianca Schneider-Häder,
DLG Competence Center Food,
Sensorik@DLG.org
Inhalt
- 1. Terminology and terms
- 2. Positioning to other elements of food integrity
- 3. List of the most frequently falsified foods
- 5. Legal environment – Integrating standards (BRC and IFS)
- 6. Risk aversion and risk prevention
- 6.1 Motivation: why is fraud carried out – linear and non-linear causal chains
- 6.2 Perpetrator profile: who falsifies and what methods are used
- 6.3 Effects of fraud: Role of chemical-physical laboratory analytics and sensor technology
- 6.4 Best practice advice on risk prevention in the company
- 7. Outlook
- Literature
- kontakt
A publication on the subject of “Food Fraud” is to be introduced with the words: “A spectre is haunting Europe – the spectre of food fraud”. The enormously increased, agitated media presence of the topic in recent years as well as the often rash and inconsistent synonymous use of the terms “food fraud”, “consumer deception” and “consumer deceit” in almost every food-related context by various organisations, institutions and in part also by companies in the food industry are leading to increasing uncertainty – not only among consumers, but also among participants in the meanwhile extremely complex value-added chain for food based on the division of labour.
In reality, food fraud is as old as mankind, even if “scandals” of the recent past may suggest otherwise. However, the explosive nature of the issue is intensified by the globalisation and fragmentation of commodity flows and processing stages on the one hand, and the demand of consumers and their representatives for complete transparency on the other. This is combined with new creative forms of fraud as well as new creative methods of analytical proof. Against this background, it is certainly advisable to work through the world of risks as pragmatically and realistically as possible in order to be able to effectively reduce the risk of unintentional and undetected “passing through” of frauds with the necessary tools.
The following expert knowledge is intended to create transparency in a compact form and provide strategies for practical risk prevention and defence.
1. Terminology and terms
The German Federal Office of Consumer Protection and Food Safety (BVL) must confess when answering the question “What is food fraud?” on its website1:
Food fraud is generally understood to be the placing of food on the market with the aim of obtaining a financial or economic advantage through deliberate deception.
[...]
The views of the European member states on this (note: on the definition of “food fraud”) differ. This is one reason why there is currently no uniform legal definition of the term “food fraud” in European legislation.
In German legislation, the term “fraud” is very precisely defined in the Criminal Code and its applicability in the sense of a criminal offence is circumscribed in detail. In contrast, (fraudulent) “deception” is an undefined term of civil law and therefore more of an administrative offence. In the complex of issues discussed here, the boundaries are fluid, and the assessment of whether a criminal offence or a misdemeanour is to be carried out by lawyers in cases of doubt on a case-by-case basis. Therefore, this publication uses the term “food fraud” throughout. This is to be understood as a collective concept, which in particular includes the elements of conscious and intentional
- Substitution of value-giving content by inferior substances
- Stretching of value-added content
- Manipulation of food of any kind
- Misdeclaration of the food and its ingredients and constituents
- Misleading presentation
- Falsification of documents for the purpose of concealing origin and/or authenticity
predominantly for the purpose of achieving a business improvement of the offender.
2. Positioning to other elements of food integrity
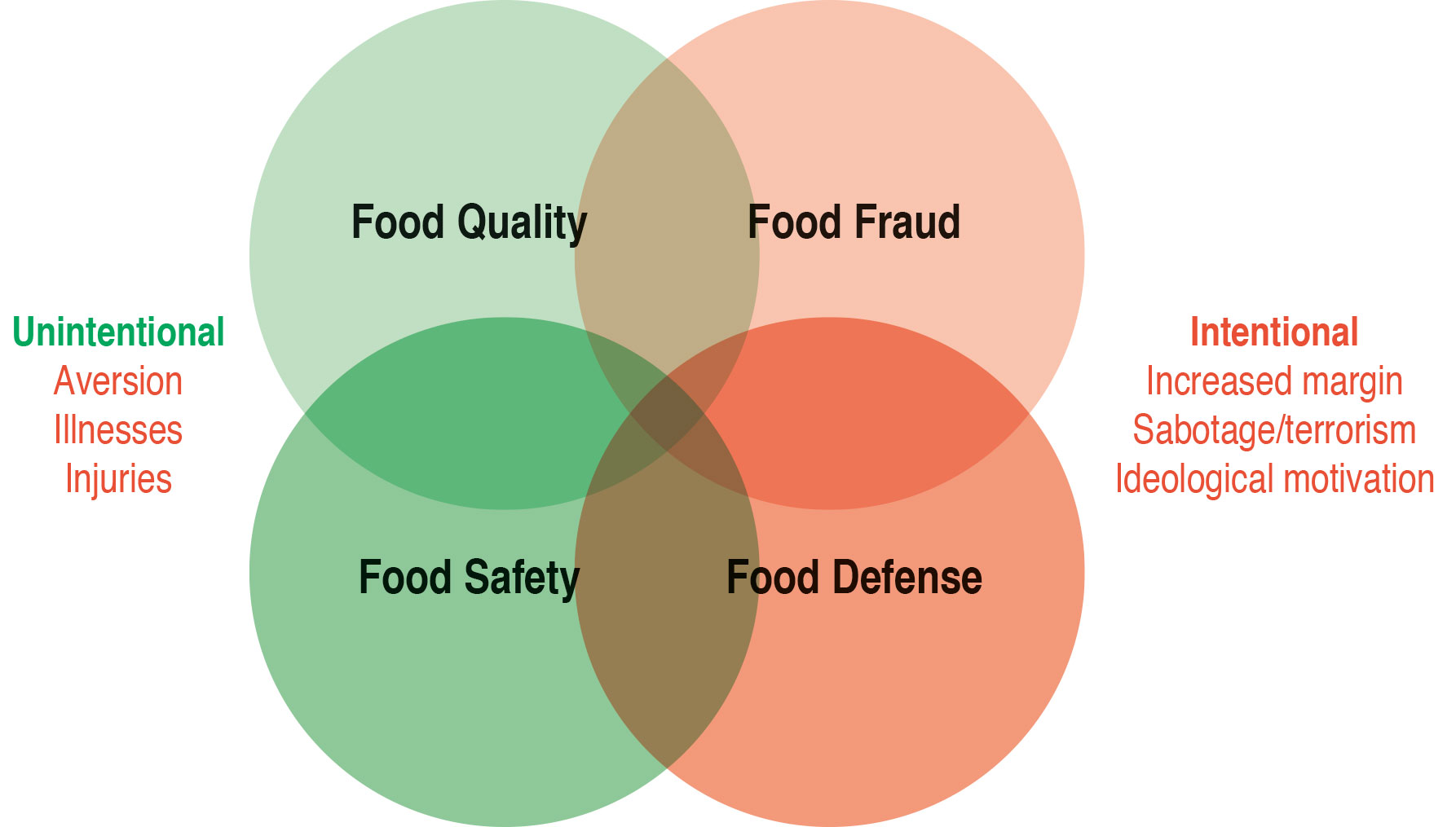
Food fraud is one of the four common components of food integrity and is now considered equivalent to food quality, safety and protection. The four thematic complexes cannot be sharply separated from each other in practice and overlap in terms of content. (See Figure 1)
Usually, the “perpetrators” are assumed to have a commercial interest, which means that quality and in particular safety are not necessarily affected in the case of a fraud (e.g. organic/non-organic, wild catch/aquaculture, regional origin). For some recent acts of fraud, the implications extend into food quality (e.g. relabelling meat after the use-by date) and even food safety. A prominent example of the latter is the melamine scandal: The addition of protein premixes to infant formula to simulate a higher protein content led to severe kidney disease in nearly 300,000 infants and at least six deaths proven in a linear-causal manner.
Fraud, contamination or sabotage of food with the aim of damaging companies or people can be ideologically or terrorist motivated and extends into the topic complex of food protection (food defence).
In the following, it is assumed that food fraud is carried out for the purpose of increasing the business margin or for other monetary motives.
3. List of the most frequently falsified foods
In a publication by Spink et.al.2, known cases of food fraud in the years 1980 to 2010 are analysed and statistically evaluated by product group. In the context of a report of the European Parliament from December 20133, these data are plausibilised with information from retail and industry associations and transferred into the following list of foods with the highest risk of adulteration (in brackets: Excerpt of known examples of frauds):
- Olive oil: (false indication of origin, mixing with old stocks, stretching with soy bean, maize, sunflower and hazelnut oil, etc.)
- Fish: (wrong species, aqua culture for wild catch, admixture of soy protein in processed fish dishes)
- Organic food: (mixing with conventionally grown products)
- Milk: (stretching with vegetable oils and water, mixing with foreign proteins and substances that simulate protein, e.g. melamine)
- Grain: (wrong variety, varietal purity, wrong origin, cultivation method, stretching with foreign substances in flour)
- Honey and maple syrup: (stretching with invert sugar syrup or sucrose syrup, addition of sugar and water)
- Coffee and tea: (coffee: origin, variety, stretching with roasted maize, stretching with malt or pulses; tea: origin, variety, stretching with used tea leaves, mixing with coloured sawdust, stretching with worthless stem material)
- Spices: (chili: stretching with marigold and marigold leaves, sandalwood shavings, dyed grass, fibres of beetroot or pomegranate, dyeing with yellow and red dyes)
- Wine: (origin, purity, vintage, addition of water, sugar, ethylene glycol, mislabelling)
- Fruit juices: (e.g. orange and apple juice: addition of non-species-specific fruit juices, pretence of “freshly squeezed” by means of opacifiers, stretching with water and sugar, addition of synthetic aromas and flavours as well as colouring agents)
4. Categorisation of frauds – “fraud quadrant”
Fraud of a product can be carried out in many ways and also in combinations of “methods”. For effective defence and prevention strategies, it is crucial to move in consistent systematics, as a) the available instruments attack at different points and b) the possibilities for fraud are so numerous that it is advisable – at least when building defence systems – to prioritise according to appropriate criteria.
A pragmatic and common classification of fraud methods and practices is made by assessing whether either manipulations are made to the final product (product manipulation) or the product is manipulated by appropriate interventions in the manufacturing process (process manipulation). Combinations are conceivable and partly necessary to cover a fraud. Depending on the specific facts of fraud, the falsified product poses a greater or lesser health threat to the end consumer. A “graduation” according to hazard potential is another dimension of the classification, so that fraud methods can be represented in a quadrant. (See Figure 2)
| Product tampering with Food safety hazard | Process manipulation with Food safety hazard | |
|---|---|---|
| • Melamine in protein mixes | • “Rework” of non-marketable goods | |
| • Peanut in hazelnut flour | • No pre-run for distillation: “higher yield” through use of methanol | |
| • Glycol in wine | • Use of industrial raw materials (e.g. fats, alcohols, acetic acid) | |
| • Arylamine dyes in spices | ||
• Hazelnut oil in olive oil | • Borderline filling quantity control | |
| • Sawdust in spices | • Glaze content for frozen goods | |
| • Plaice instead of turbot | • Increase in the proportion of external water | |
| • Conventional for organic goods | • Maturation time for hard cheese | |
| • Falsification of documents | • Utilisation of specification tolerances | |
| • Playing with analytical measurement uncertainty | ||
| Product manipulation without Food safety hazard | Process manipulation without Food safety hazard |
Figure 2: Quadrant of possible fraud methods for food
5. Legal environment – Integrating standards (BRC and IFS)
The basis for all regulations in the area of food integrity is the “Regulation (EC) No 178/2002 of the European Parliament and of the Council of 28 January 2002 laying down the general principles and requirements of food law, establishing the European Food Safety Authority and laying down procedures in matters of food safety4”. Here it is explicitly stated in Chapter II (General Food Law) in Article 8 (Protection of Consumer Interests):
(1) Food law aims to protect the interests of consumers and must enable consumers to make informed choices about the food they consume. Here the following must be prevented:
a) Practices of fraud or deceit
b) Food fraud and
c) Any other practices likely to mislead the consumer
All laws, regulations, control provisions and guidelines in this context are derived from this Ordinance. The emerging legal situation regarding food fraud is heterogeneous and fragmented. There is no harmonised regulation on food fraud under European law, as the legal regulation of penalties and sanctions falls under the sovereignty of the EU member states and the European legislator can only demand that the member states formulate corresponding legal regulations. Nevertheless, there are a number of descriptive regulations that are formulated in a standardised European way. These can be found among others:
- In Chapter II, Article 16 of Regulation (EC) No 178/20023: Prohibition of deception through the presentation of a foodstuff
- In Chapter III, Article 7 of Regulation (EU) No 1169/20115: Fairness of information practices
- In Section 2, Sec. 11 of the Foodstuffs, Commodities and Feedstuffs Code6: Rules for protecting against deception
The European Food Safety Authority (EFSA) is the institution that brings together regulations for the member states in the context of production hygiene, declaration, safety and traceability of food on the Community level.
At the European and also the national level, the partly abstract regulations are flanked by further regulations which apply to more precisely defined circumstances. This includes, for example:
- The Food Hygiene Regulation (EC) No. 852/20047, which contains the application of a HACCP system as a central requirement
- Regulation (EC) No. 853/2004 on specific hygiene rules for food of animal origin8
- Regulation (EC) No. 2073/2005 on microbiological criteria for foodstuffs9
- The Animal Food Hygiene Ordinance (Tier-LMHV)10 etc.
Thematically, the national and European legal regulations overlap and intermingle, and in part they build on each other or reference each other. This poses a challenge for consistent implementation by companies, especially since the underlying texts are in part very formal and abstract and lack concrete implementation instructions.
Relevant standards and associated quality management systems attempt to integrate legal requirements and elements of safety as well as their practical implementation among the participants in the value chain, to standardise requirements, especially of the end consumer, and to ensure food integrity pragmatically with the help of very detailed lists of requirements and tests. The penetration of the food production and processing industry, especially in the private label sector, is so complete that, with the possible exception of medium-sized producers of regional goods, almost every producer is subject to these standards.
The driving force behind the establishment of these standards in Europe – as the last element in the value-added chain and as the distributor of the majority of the goods produced – is the Retail Food Trade (LEH), represented for example by the German Retail Federation (HDE)11 and by its Anglo-Saxon counterpart, the British Retail Consortium (BRC)12. The most important current standards are the BRC Global Standard for Food Safety Version 813 (BRC Food 8) and the International Featured Standard Version 7 (IFS Food 7).
The Food Safety System Certification 22000 (FSSC 22000) standard, which is based on ISO 22000 and was published in version 5.1 in November 2020, is formally independent of the intellectual property of a particular interest group.
Organisations such as the Global Food Safety Initiative (GFSI) in particular strive to make food safety and food integrity management systems comparable by means of a higher-level set of requirements (GFSI Guidance Document) and promote mutual recognition. Among other things, the GFSI establishes equivalence between FSSC 22000 V5.1, BRC Food 8 and IFS Food 7. For suppliers of private label products for the German Retail Food Trade (LEH), IFS Food 7 or its derived variants will be the the most widely used (application of IFS 7 will be obligatory from July 2021).
Although protection against food fraud and its sanction are in principle laid down, demanded and preconceived in the laws and regulations, current quality management systems and standards still focus predominantly on food quality and food safety, and in part also on food protection (food defence), i.e. on specifications, claims, declarations and conformity of raw materials and end products with the regulations, conventions and ordinances, in particular to set limits for microbiological loads, contaminations and residues. The IFS Food 7 addresses the protection against food fraud in a rudimentary way in chapter 4 “Operational Processes”, section 4.20 “Food fraud”. It says in 4.20:
- The responsibilities for a food fraud vulnerability assessment and mitigation plan shall be clearly defined. The responsible person(s) shall have the appropriate specific knowledge and full commitment from the senior management.
- A documented food fraud vulnerability assessment shall be undertaken on all raw materials, ingredients, packaging materials and outsourced processes, to determine the risks of fraudulent activity in relation to substitution, mislabelling, adulteration or counterfeiting. The criteria considered within the vulnerability assessment shall be defined.
- A documented food fraud mitigation plan shall be developed, with reference to the vulnerability assessment, and implemented to control any identified risks. The methods of control and monitoring shall be defined and implemented.
- The food fraud vulnerability assessment shall be regularly reviewed, at least annually, and/or in the event of increased risks. If necessary, the food fraud mitigation plan shall be revised/updated accordingly.
In a dedicated guideline for implementation assistance is given for systematically breaking down the overall risk into more manageable sub-risks. Complexes of topics for the assessment of risk exposures are mentioned:
- History of food fraud incidents
- Economic factors
- Facilitated opportunity for fraudulent activity
- Complexity of delivery chain
- Current control measures
- Trust in suppliers
The enactment of IFS Food Standard 7 requires companies to make enormous efforts to be able to present a robust risk mitigation plan to the auditors.
6. Risk aversion and risk prevention
Many publications and lectures focus on physical-chemical analysis to combat and defend against food fraud. But this is (much) too short-sighted: when the analysis “takes effect” – if it does so robustly enough and the interpreter also has the courage to articulate this – everything is already over. A possibly non-marketable or even dangerous “food” has been produced, valuable raw materials have been irretrievably wasted and trust in people, companies, names, brands, products and countries has been shaken. In terms of quality assurance, laboratory analytics supports a sorting and selection process and with it any necessary corrective action: e.g. sanctions such as contractual penalties for the supplier, threat of delisting, change to alternative suppliers for the purpose of ensuring availability, etc.
An effective preventive measure and preventive strategy starts much earlier and, above all, differently. It asks about motivation, a possible “perpetrator profile”, technique and execution of the fraud and – in the end – the effect of the fraud, which can possibly be proven beyond doubt with the help of suitable laboratory analytics. Only with the help of a comprehensive approach is the entrepreneur in a position to be able to systematically identify possibilities for frauds of the products he/she uses and to take appropriate measures. Focusing on known scandals in retrospect only helps to a limited extent and does not prevent the unintentional passing on of creative new frauds.
6.1 Motivation: why is fraud carried out – linear and non-linear causal chains
Understanding motivations requires a good understanding of the products used or traded, if possible across several stages of the preceding value chain, which, especially in the case of international supply chains, is knowledge that a company must build up over many years with a great investment of time and resources or must procure from service providers.
The understanding of the products and goods includes not only the technology, the quality assurance measures for preliminary products and within the production process, the certificate situation, the causal dependence on external factors, etc., but also and in particular the supplier’s environment in the dimensions: culture, qualifications of key personnel, financial situation, political environment.
The simplest motivation for fraud, and therefore the shortest linear causal chain, is greed for additional margin. Especially products for which end consumers are willing to pay high prices are spectacularly at risk, for example, of being stretched or falsely declared. Virtually all product groups can be affected, including of course the “top 10” mentioned above: Fine fish, meat, oils, wines, spirits, cheese, vinegars, honey, cocoa, coffee and tea of origin, spices, etc., but also bulk products such as baby food with the well-known frauds by substituting a value-giving ingredient with an inferior chemical substance. The resulting analytical question is one of authenticity (origin, year, variety, species), quantity, proportions and purity (no extenders).
Another key motivation is to “increase” the quantity of goods and commodities available with high demand but fluctuating availabilities. Frequently accompanying factors are price pressure and price fixing for the products concerned. The simplest still linear causal chains are found in agricultural products, e.g. cereals, fruits, nuts, olives. Today, crop yields can be very reliably associated with and predicted by time series for temperature and precipitation. Frost in spring during the flowering of hazel and apricot in Turkey (as a major producing country) will mean shortages of hazel and apricot in autumn. Prolonged heat and long summers during the ripening of the olive can favour a secondary population of a pest that either greatly reduces the viable crop or encourages unplanned insecticide use with possibly insufficient waiting time before harvest. For cereal crops in the 40th to 55th latitudes, rainfall distributions and temperatures in the first quarter and in June are decisive for the harvest result15. Here as well, the purity will be ensured (stretching) and quality parameters checked (indications of inferior or unsuitable goods, contaminants, mycotoxins, rancidity, sensory peculiarities such as roasted notes in “fresh” hazelnut flour), as well as pesticide residues (conventional for organic, insufficient waiting times).
The motivation for food fraud can also be based on a situation threatening the existence of the perpetrator. The underlying causal chains are not necessarily related to “food” and are therefore indirect or non-linear. The explanation is given using two fictitious, freely invented examples:
Fictive example 1:
In an agrarian country with more than 40 % of the land in agricultural use, especially by family businesses, farming is still done traditionally and with the use of horses to pull farm implements. The country has a high export share of agricultural products to industrialised countries with large customers. Following the trend of improved animal welfare, these bulk buyers now demand the renunciation of the use of horses in the production of the goods purchased. Compliance with the requirement is checked in unannounced audits; lack of compliance is subject to severe sanctions. A negative spiral begins: Liquidity is needed to mechanise the production processes. For these, the buyers would have to accept the goods traditionally produced by means of animal input, which they do not do. Banks see a big risk and refuse financing. The horses that can no longer be used become a mere liability and an additional cost factor.
The solution comes from an unnamed organisation that has contacts in the meat processing industry via many detours. This organisation offers farmers facing extinction to take the workhorses for a fraction of their actual value and trade them in for used tractors with rudimentary accessories. A large number of barter transactions take place and trade with the wholesale buyers – now fully compliant – regains momentum. There is uncertainty about the whereabouts of the horses. They were of course not “tagged” and are therefore not traceable, nor does anyone raise questions about this.
Fictive example 2:
In a country with a regionally strong dairy industry, a particular cheese is handmade in a particular region using traditional methods. A special quality feature of the cheese is the use of regionally organically produced raw materials and the price-determining, precisely defined long maturing period of – depending on the quality – up to several years. For some time now, the discounter retail trade has discovered the product as a premium item for itself and demands large quantities – naturally with price expectations that require a partial mechanisation of the cheese production process, as well as a substantial increase in controlled storage capacities. The local banks readily support this phase with generous loans. Business is going great for cheese producers with high levels of customer satisfaction until ... ATMs of the local banks are “temporarily out of order” and transfers of debts to, for example, the milk suppliers are not executed despite a credit balance on the account. It soon turns out that the banks have no liquidity left and are broke, and with them the customers who urgently need this very liquidity to continue financing their current business and livelihood. A new way must be found to collect money and use it in a sound bank.
The way out is a re-evaluation of the enormous amount of tied-up capital, which is blocked in huge warehouses in the form of ripening cheese towards the delivery date. On closer inspection, the prescribed ripening period can only be proven by documentation, and between a cheese that has been ripened for the prescribed 24 months and one that is tasted after, say, 19 months, there is no perceptible difference in sensory terms beyond the natural “spread”. So why not, in a pinch, use the equivalent of five months’ production before the end of ripening to restore liquidity and service any customer complaints that may arise from the “iron reserve” of fully ripened goods?
Common to both fictional examples is a) an indirect trigger for food fraud and b) the lack of a direct revenue-enhancing incentive. The clarification of such non-linear causal chains and use for risk detection and preventive risk defence is complex due to the multitude of conceivable triggers. It requires a lot of experience, instinct, creativity and an enormous degree of interdisciplinarity, as the patterns of such incidents strongly resemble “disasters” in other industries not related to food production. This expertise is not usually available in companies, but can be utilised by service providers.
6.2 Perpetrator profile: who falsifies and what methods are used
It would be presumptuous to list all conceivable “forger types” and methods at this point, nor would it be expedient. Already known adulteration techniques, especially in the above-mentioned “top 10” product groups, are repeatedly attempted and can be well prevented and intercepted through good commodity knowledge, strict supplier and specification management, as well as adapted targeted physical-chemical laboratory analysis. The degree of residual risk ultimately depends only on the budget for travel costs, for unannounced audits and for laboratory analyses.
However, a certain class of offenders requires special consideration, namely offenders with a knowledge of laboratory analytics and the interpretation of analytical results. Here, two mechanisms of deception must be fundamentally distinguished:
Mechanism 1: Deception of analytics
This potential group of perpetrators has precise knowledge of the common methods used to determine and also to quantify typically cost-driving value-added components of a foodstuff and uses this knowledge to deceive, e.g. by substituting the value-added component with inferior substances. Particularly at risk are ingredients and formulation components whose determination is carried out indirectly, for example because direct detection is too costly or perhaps not even possible at all.
Example: the value-added protein content of a food or a precursor thereof is determined by the Kjeldahl method16 or related derived methods. Essentially, the sample is digested with a self-confident chemical – namely concentrated sulphuric acid – the bound nitrogen is converted into free ammonia using NaOH and then titrated. The method determines the nitrogen content in the sample. Assuming that the nitrogen comes from the protein (with an average nitrogen content of, for example, 16 %), the protein content can be calculated back to the protein amount by means of a factor (e.g. 6.25). The factor is based on literature values and has a considerable range. This method for quantitative protein determination is omnipresent.
Almost any organic substance that contains nitrogen and can be broken down in sulphuric acid can in principle serve as a protein substitute without this being noticed in the analytics used. In 2008, dairy products, especially baby food, were found in China in which melamine C3H6N6, a raw material for synthetic resin production, was used to simulate a higher protein content than was actually present in the product. Melamine is soluble in water, comes in the form of a white powder and is easy to mix in. Its price is a small fraction of that of protein premixes or pure protein raw materials, and even at low concentrations it simulates a higher protein content. The wet chemical methods described above could not detect the fraud. Only widespread severe kidney disease in infants and young children finally led to the unravelling of what is now known as the “melamine scandal”, a widespread food fraud. The “technical” heads of the perpetrators had in-depth knowledge of the dairy industry and even ran a chemical laboratory (actually for quality assurance) to study the effect of melamine admixture in milk on the analytical result and to find a “suitable” dosage in a negative sense17, 18.
Detection of adulteration or contamination with melamine requires separately developed analytical methods (typically: LC-MS/MS), which search specifically for melamine and structurally related molecules such as cyanuric acid, ammelin or ammelide, but do not work reliably or at all for other nitrogen-supplying substances. The Kjeldahl method remains the preferred method for (indirect) protein quantification in food.
Mechanism 2: Deception of the evaluation of measurement results – Playing with measurement uncertainties
The potential perpetrator group trusts in the inconspicuousness of frauds in the trace area. Particularly at risk are, on the one hand, products for which there is great demand and which are produced or harvested seasonally in large quantities. Substitution of valuable components, stretching with inconspicuous foreign substances, blending with products of inferior quality but of the same species, etc. in low concentrations are common techniques of adulteration. The economic advantage is calculated by the large volume of the product, usually “container goods”. On the other hand, however, composite products, which are usually defined by specifications, ingredient lists and recipes, also come into question for this class of adulteration. Smaller “scatter” in the recipes is certainly unavoidable, but the deviations from the nominal recipe are not always equally distributed “upwards” and “downwards”. In the sense of deception, tolerances are systematically exploited “downwards”.
These frauds can hardly be countered with laboratory analysis alone. Every measurement result is subject to a measuring uncertainty, which results from the method itself, the homogeneity, the consistency of the excipients used, etc. There are standardised procedures for determining the measurement uncertainty, which are ultimately based on continuous probability distributions. Convention is the use of the
- Simple measurement uncertainty: contains 68.3 % of all measured values, as well as the
- Expanded measurement uncertainty: contains 95.5 % of all measured values.
Exceeding of limit values, utilisation of maximum quantities and specification violations are usually assessed as such if the measurement result exceeds or falls below the reference value, taking into account the expanded measurement uncertainty. An approximation to the reference value in the negative sense does not lead to a complaint in most cases. The fraud is not noticed or is suspected, but supposedly cannot be proven due to a lack of “hard” data.
6.3 Effects of fraud: Role of chemical-physical laboratory analytics and sensor technology
Fraud is detected in the laboratory using two completely different approaches:
Approach 1: „Targeted analyses“
The inspection of goods and products for known frauds (i.e. those that have already occurred in the past) is carried out using targeted analysis methods. The underlying question is: “Does the product contain fraud x?”. Example questions:
- Does this meat preparation contain more than 0.05 % horse meat?
- Does this milk powder contain melamine?
- Does this olive oil contain hazelnut oil?
- Does this olive oil come from Italy?
- Does this coffee, declared as Arabica coffee, also contain Robusta components?
- Does this organic product contain pesticides other than those authorised for organic farming in (EC) No. 834/2007 and (EC) No. 889/2008 as amended by (EU) No. 2016/673?
- Does this hazelnut flour declared as “fresh” contain proportions of roasted hazelnuts?
- Does this Aceto Balsamico di Modena contain acetic acid from sugar beet?
- Does this honey contain cane sugar or saccharification products from maize?
- [...]
The optimal analytical method to be used depends on the specific problem for a product, a raw material, a matrix and the target substance. The spectrum of available techniques and methods is immense and ranges from simple wet chemical and molecular biological investigations to conventional as well as high-resolution chromatographic methods and physical techniques such as the analysis of stable isotope ratios. What all techniques and methods have in common is their retrospective character: the laboratory knows what to look for. The target substance is known.
Approach 2: „Non-targeted analyses“
A completely different approach is to search for deviations from the optimal product in as non-targeted a manner as possible, without first knowing or specifying these deviations in more detail. A common procedure is to characterise an authentic and optimal product analytically as comprehensively as possible as a reference (fingerprinting), in order to then examine the results of the product to be sampled for characteristic agreement as well as for clear deviations from the reference. If the possible fraud can already be narrowed down and a suitable non-directed screening method (“non-targeted analyses”) is available, a positive hypothesis can also be tested directly. The underlying question is: “Is the present sample the substance y with a certainty > x %?”.
Examples:
- Does this meat preparation contain DNA of animal species other than beef and pork?
- Is pure milk powder concerned?
- Does this coffee contain only Arabica varieties as declared?
- Is this olive oil equivalent to the reference oil?
- [...]
The non-targeted methods may leave the realm of established official testing methods, although the techniques used are quite robust, fully validatable and also accreditable. Many of the methods, especially those based on nuclear magnetic resonance (NMR), require a large number of authentic, precisely described reference samples to build reference databases. Obtaining a representative figure is very costly. These databases are set up decentrally for different commodity groups by different organisations, companies, laboratories and working groups and are usually proprietary. Databases are available for juice, wine, honey and olive oil, among others.
Special role of sensor technology in the non-targeted methods
The role of sensor technology in detecting fraud cannot be overestimated. It can be understood as a complex, simultaneous recording and evaluation of numerous chemical properties characterising the product under investigation. Deviations and atypical characteristics consistently noticed and described by the experienced team are the starting point for concrete hypotheses, which are then tested with targeted methods. For example, sensory analysis has long been used to verify the declared grade of olive oils.
In the above fictitious example of cheese that has been ripened for too short a time, analytical proof of deception is hardly possible. Today, there is no analytical method that could determine the ripening time of a cheese with sufficient accuracy. Comparative sensory analysis with (as authentic as possible) comparative products, carried out by trained test persons conditioned to cheese, is a reliable way to notice and describe deviations from the “optimal product”. In cases of suspicion where there is still uncertainty about the choice of suitable analytical methods, sensory analysis is usually the starting point for further, now targeted investigations.
Example 1: 1H-NMR as a targeted method for the proof of authenticity of olive oil
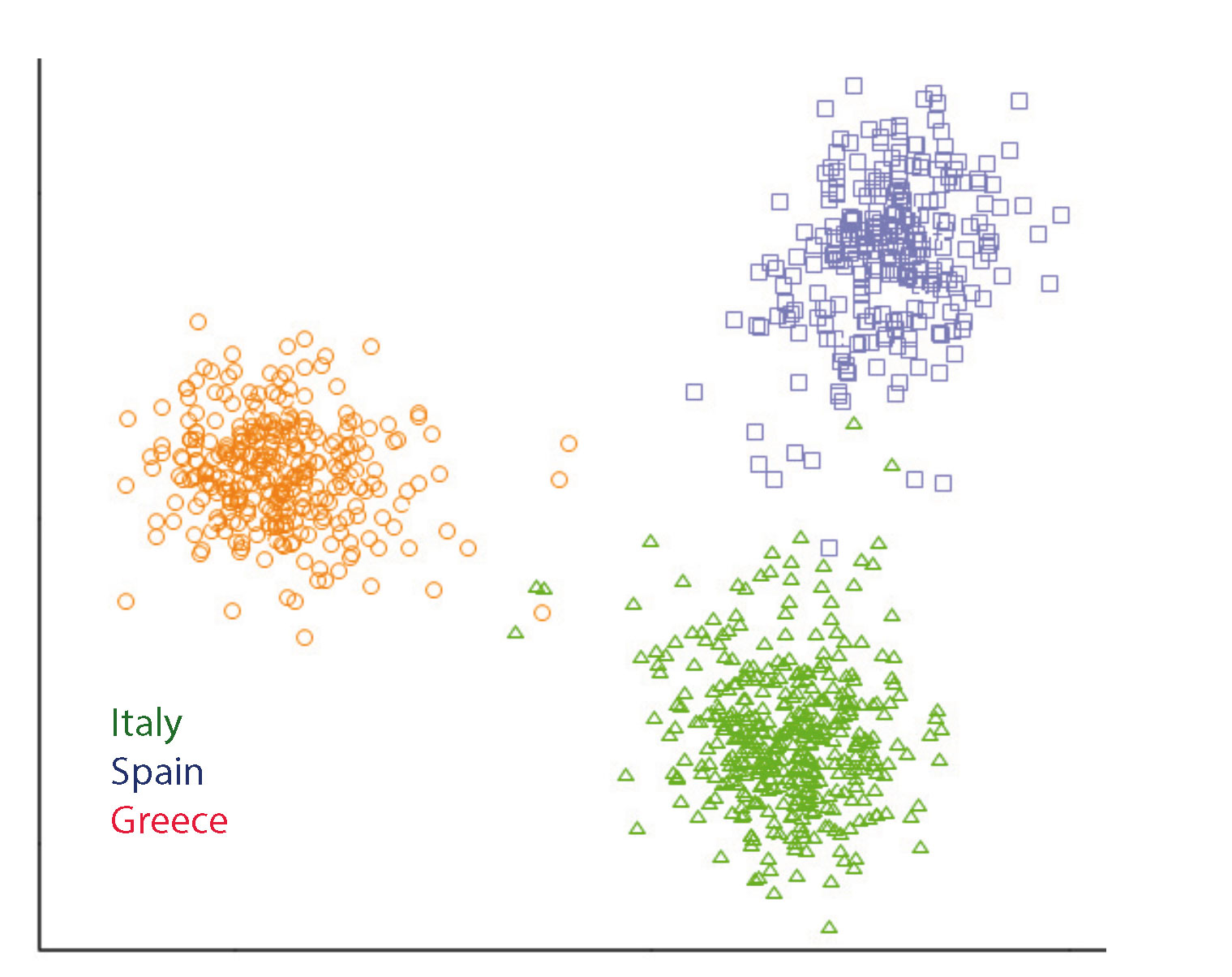
The 1H-NMR method can verify origin information for European olive oils by means of Eurofins profiling, which has been accredited since mid-201719. The underlying database contains approx. 1,000 authentic oils from the main growing areas in Italy, Greece and Spain, varietal origins (olive varieties) and data over several harvest periods. More than 95 % of the oils can be correctly classified (cross-validation). In a highly simplified representation, oils from the countries of origin can be distinguished from each other. (See Figure 3)
A targeted question (hypothesis test) “is the origin of this olive oil Italy?” can be answered reliably with this method and presentation. The method is used for valuable oils of origin and in the early stages of the value chain to verify the authenticity and purity of mother lots. For blends of two pure oils from different countries of origin, the method can still be used to determine the proportion. The method cannot be used for more than three components today.
Example 2: 1H-NMR as a non-targeted method for the detection of olive oil fraud
In the volume trade, “blends” of olive oils are often used, i.e. mixtures of several olive oils of different origins. Almost all “parameters”, such as country, region, olive variety, etc., can vary. Trying to characterise these “blends” by means of directed analyses is not possible due to the many possible degrees of freedom. However, the 1H-NMR method makes it possible to record the properties of the sample oil and to create a reference from it. This process is much less time-consuming than building a precisely described reference database, as only the fingerprint of the individual “optimal” oil is recorded. In the non-targeted analysis, deviations from the “optimal” oil are now detected without characterising them in more detail (in the first step).
The 1H-NMR is sufficiently sensitive both to changes in the blend (i.e. changes in the composition of the olive oils used) and to the use of foreign oils.
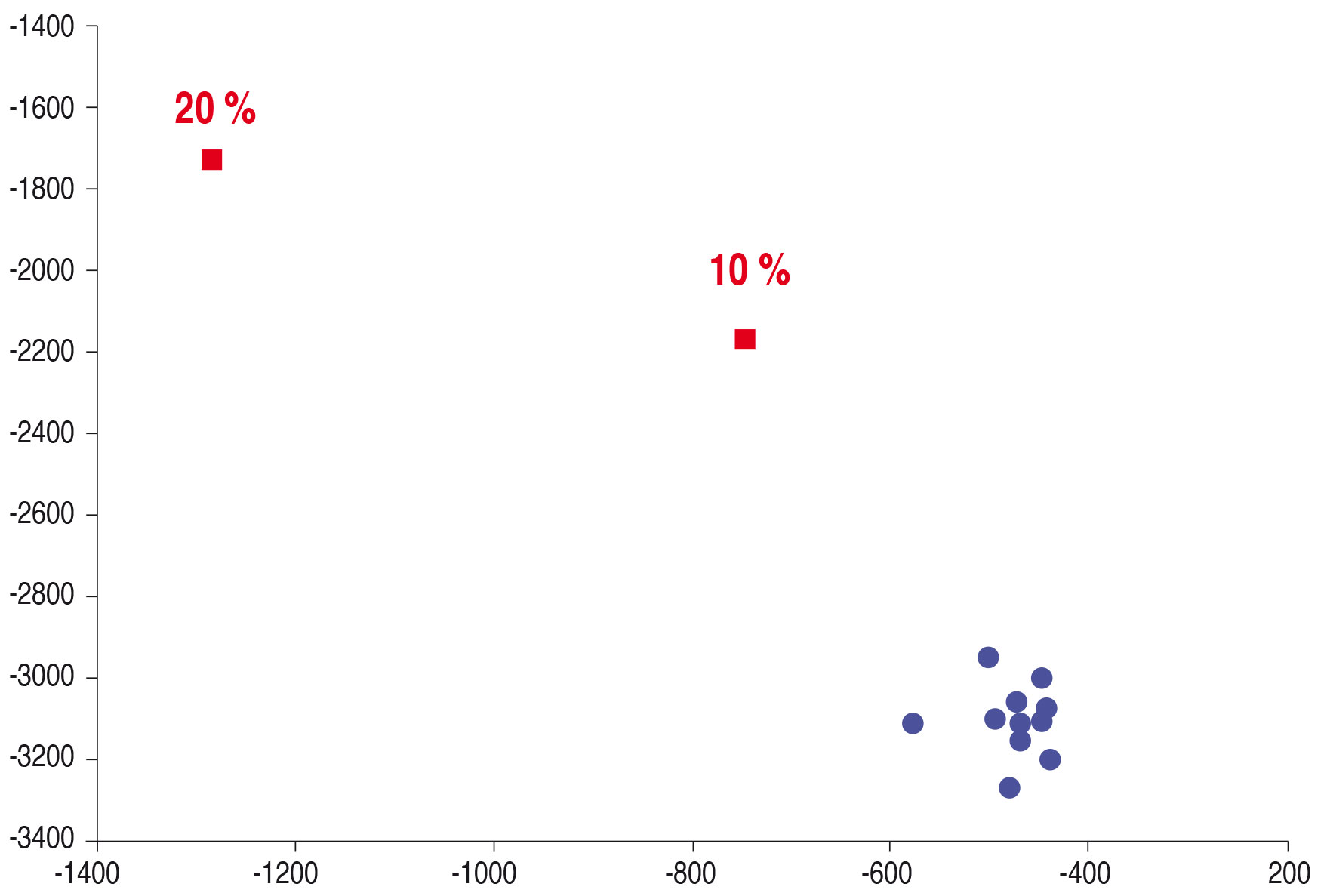
For the results shown in Figure 4, ten bottles of a commercial blend were used to create the reference (blue). The position of the blue reference points is almost independent of the age of the oil (monitoring period > 6 months). Both an addition of 10 % or 20 % of another commercially available blend and a fraud of 10 % and 20 % by foreign oil (e.g. sunflower or rapeseed oil) can undoubtedly be identified as a deviation.
In the first step, the 1H-NMR method in this application shows the unspecified deviation from the reference. A simultaneous assessment of whether it is a change in the blend or the addition of tramp oil is the subject of current method development.
6.4 Best practice advice on risk prevention in the company
There is much supporting literature to the established standards and norms related to food integrity that assists in the implementation, refinement and optimisation of an already implemented standard. Therefore, the implementation
of a standard will not be discussed here. Rather, the aim is to provide practical advice on how prevention of food fraud
can become part of the corporate culture. So in addition to the anyway obligatory topics of standards and norms,
some tips.
The basic elements of effective and far-sighted risk prevention are:
- Resources
- Attention and qualification
- Curiosity
- Creativity
- Interdisciplinarity
- Perseverance and consistency
Resources and consistency of corporate values
In an ideal world, many elements of risk prevention are part of the company’s routine. Often, however, basic work has to be done, and resources are also needed for further and new development of systems. Management must provide and support these freedoms and resources and cascade this support through the hierarchy. For manufacturers of complex products with international procurement, it has proven useful to establish a dedicated position for the coordination of prevention measures (risk manager). This position is a staff position of the management – either “stand alone” or as part of the quality assurance. The line must continue to set a consistent value corridor that cannot be expanded by third parties and that does not conflict with, for example, availability bottlenecks or price expectations of the main customers. Defence and prevention strategies have long cycles until they show an effect and “take hold”. Volatility in the underlying values is counter-productive.
Qualification, interdisciplinarity and attention
Involve your employees in risk prevention across disciplines and encourage employees to communicate anomalies, observations and information to the risk manager. The better qualified your employees are and the more they are integrated into the overall context, the more likely they are to develop hazard instincts and provide crucial information.
Delivered goods not as usual? Packaged differently? Labels removed or taped over? Goods on the truck “for another customer” that should actually be disposed of? Worrying figures in the last annual accounts? Employees of the supplier tell your staff on the phone about fire in the administration building? Media report on unstable banking or political situation in the supplier’s country?
Qualification includes, in particular, an in-depth understanding of the products manufactured (or marketed) in-house and the preceding value chain for raw materials, ingredients, semi-finished products, etc. Which value-giving attributes of the goods are passed on and which risks?
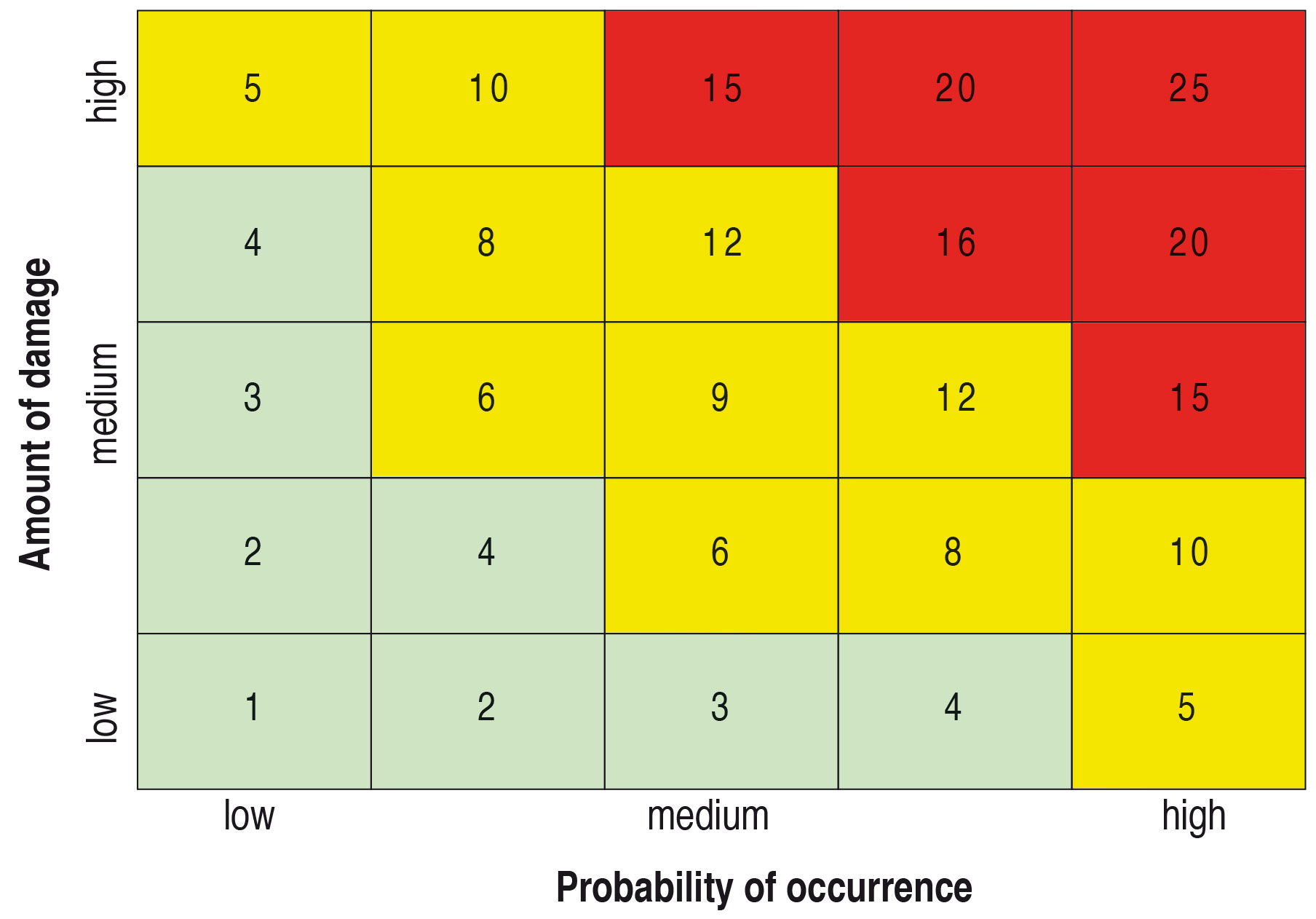
Develop pragmatic specifications for your goods to be procured and assess them in terms of risk, e.g. according to the standard matrix procedures (see Figure 5) and do this a) for different risk classes separately, if necessary, and b) dynamically, i.e. review the risk assessment regularly and/or when new information becomes available.
Become a moving target for a food falsifier. Enter into discussion with your laboratory or laboratory service provider with this dynamic set of risk assessments and develop risk-oriented analytical test plans and also dynamise them in sync with your risk assessment. Be sure to include sensory testing as a powerful undirected method. Expand the scope of test methods in quality assurance and also allow non-official and newly developed methods. Allow the laboratory to adapt to your questions and optimise methods for your products.
Regularly bring together your buyers, quality assurers, controllers, technologists and, if necessary, external parties and analyse the macro-economic situation of your suppliers (“the market”) and assess it with regard to emerging risks. Will there be quality losses and shortages due to weather, for example? Can alternative sources be switched to? Does the risk profile then remain unchanged? What commercial and quality-related effects are to be expected? Do test plans need to be adapted and/or the test frequency increased?
Make prevention strategies against food fraud part of your sustainability programme: effective prevention prevents fraud and therefore saves food and raw materials from possible destruction.
Accompany all your measures with qualified legal work and solid contracts with your suppliers and service providers.
Curiosity and perseverance
The transparency of upstream complex international commodity flows and value-added chains usually decreases rapidly. You can only counter this by building long-term business relationships with your suppliers and service providers and maintaining them critically. Always be suspicious (but not paranoid). Every guidebook on supply chain management contains the reference to simplifying the supply chain, so here as well: try to source your goods as close to their origin as possible from a small number of suppliers who you build (and educate) into long-term partners.
Visit your suppliers regularly with an interdisciplinary team, even independently of formal audits. Be curious and take advantage of every opportunity to visit production, goods receiving, etc., even unscheduled. Always watch out for implausibilities. Mentally compare similar suppliers and develop a sense of what is “normal”. Show interest in your supplier’s organisation and environment. What moves it, what is it dependent on, what does its own supplier world look like? Gain more transparency about the “upstream” supply chain with the help of your supplier.
Take an interdisciplinary approach to supplier audits, inspections and visits. You can learn a lot without asking. Examples: Is the quantity of goods in production and in the warehouse plausible with economic figures (internet research) for realistic turnover figures? Are there details in production that do not fit with an otherwise LEANed process? Temporarily stored goods? “Restricted” goods outside the quarantine area? How is any existing “rework” process implemented? Does the associated documentation match the scrap and defective production data? Are waste balances plausible? Does your supplier have the same level of attention to food fraud that you have? If so, have it show you examples of where the supplier has “intercepted” falsified goods. What is it particularly proud of in this context?
It takes many years to build up a wealth of experience. Document knowledge, experiences and findings – in whatever form. The process of learning never stops; knowledge and experience do not become obsolete. In some areas, you can buy into expertise from service providers. Fraud techniques that have supposedly not been used for decades and the control of which has disappeared from today’s test plans can become “in” again.
Creativity
Explain your product to friendly third parties, what it is made of and how it is created. Let the third parties develop ideas for deceptions. Invest a few consultant days for what is called a “friendly hacker” in IT security: Experts – preferably with an interdisciplinary background – who “virtually” deceive you, attack your prevention system and detect vulnerabilities. Ask for virtual stress tests: How does your organisation react when certain procurement markets disappear or prices and counterfeit risks increase due to catastrophic harvests? Is it possible that in these cases the tolerance for qualitatively questionable goods increases in favour of availability? Organise creative competitions among the staff with the aim of developing practical and effective fraud ideas. Reward the “best” ideas.
By applying all these practical tips, your prevention system will become more secure and “dense” against fraud attacks at an accelerated rate.
7. Outlook
Without doubt, analytical methods that target known frauds are becoming more reliable, more sensitive and increasingly established in routine use to safeguard against known risks. This retrospective approach will never lose its important role in basic protection against fraud, but by its very nature offers little protection against new creative attempts at fraud.
Non-directional methods, combinations of methods and also the confident use of organoleptic methods with the approach of detecting deviations from a “reference product” are powerful tools for detecting frauds, even if further investigations are subsequently necessary to narrow down the possible nature of the fraud.
According to the author, great potential for effective prevention techniques lies in the use of data and information along the value-added chain and the simulation and evaluation of possible causal chains. There is no shortage of data and information; in all modern food-related technologies, activities, plants, products and transports are digitally networked with each other (Industry 4.0 approach) in order to exploit optimisation potential along the value-added chain and achieve transparency. Significant challenges exist in the appropriate aggregation of data, much of which is sensitive and contains proprietary information, and the overarching interpretation in terms of potential risks to the product at different stages of completion. For the latter, an interdisciplinary perspective once again helps. In other industries, similar issues exist with abstract but demonstrably effective counter strategies (e.g. aviation: “bogus parts” and “disaster prevention”), parts of which can be transferred to modern food production with some creativity. The future of defence against fraud attempts lies in solid basic protection through qualification and the implementation of new ideas for proactive prevention in order to be one step ahead of the falsifiers “next time”.
Literature
- https://www.bvl.bund.de/DE/01_Lebensmittel/03_Verbraucher/16_Food_Fraud/02_Was%20ist%20Lebensmittelbetrug/Was%20ist%20Lebensmittelbetrug_node.html;jsessionid=E152CD0E11E86033DC05D1539C35CD38.2_cid332 (Stand: 17.04.2018)
- Development and Application of a Database of Food Ingredient Fraud and Economically Motivated Adulteration from 1980 to 2010/Moore, J., Spink, J. und Lipkus, M. Journal of Food Science, 2012, Volume 77 (Number 4), S. R118-R126.
- www.europarl.europa.eu/sides/getDoc.do (Stand:17.04.2018)
- http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=OJ:L:2002:031:0001:0024:DE:PDF (Stand: 17.04.2018)
- http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=OJ:L:2011:304:0018:0063:de:PDF
- https://www.gesetze-im-internet.de/lfgb/__11.html
- http://eur-lex.europa.eu/legal-content/DE/TXT/PDF/?uri=uriserv:OJ.L_.2004.139.01.0001.01.DEU
- http://eur-lex.europa.eu/legal-content/DE/TXT/PDF/?uri=uriserv:OJ.L_.2004.139.01.0055.01.DEU
- http://eur-lex.europa.eu/legal-content/DE/TXT/PDF/?uri=uriserv:OJ.L_.2005.338.01.0001.01.DEU
- http://www.gesetze-im-internet.de/tier-lmhv/BJNR182800007.html#BJNR182800007BJNG000100000
- https://www.einzelhandel.de/
- https://brc.org.uk/
- https://www.brcglobalstandards.com/brc-global-standards/food-safety/ (alle Stand: 17.04.2018)
- https://www.ifs-certification.com/images/standards/ifs_food6_1/documents/standards/IFS_Food_V6_1_de.pdf (Stand: 17.04.2018)
- Michael Horsch, Managing Director of Horsch Maschinen, personal notification of 23/01/2017
- Johan Kjeldahl, Neue Methode zur Bestimmung des Stickstoffs in organischen Körpern, Zeitschrift für Analytische Chemie, 1883
- http://www.chinadaily.com.cn/china/2008-10/10/content_7095739.htm,
- http://www.chinadaily.com.cn/cndy/2008-12/27/content_7345964.htm, u. v. a. m.
- O. Winkelmann, T. Küchler, A. Bendini, D. Garcia Gonzalez, T. Gallina Toschi: Tailored Sample Preparation for Olive Oil Analysis by 1H-NMR: Applications in Sensory Evaluation and Origin Classification, „Oleum“ project 635690 of the European Union‘s Horizon 2020 research and innovation programme.
Kontakt
DLG-Fachzentrum Lebensmittel • Bianca Schneider-Häder • Tel.: +49 (0) 69 24 788-360 B.Schneider@DLG.org